In the current digital era, mobile applications are unquestionably a necessity for everyone and have a very wide range of functions. Where one can use these applications for communication, entertainment, business, and shopping among other uses. The application usage has led to the evolution of the concept of mobile security.
Therefore, it’s crucial to implement rigorous mobile app security testing and adhere to established mobile app security standards to protect user data. It's thus critical to carry out deep application security reviews to protect user data.
This blog will deal with factors that relate to mobile security methodologies, potential risks, and recommendations for keeping users’ information secure. It is a source that provides access to many user profiles on a very large scale, ensuring mobile security application standards become crucial.
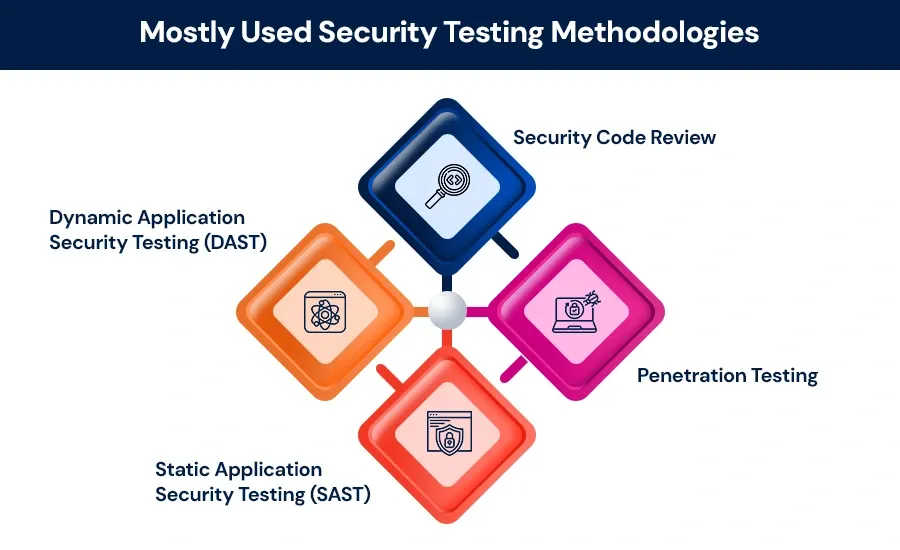
Main Security Testing Methodologies for Mobile Applications
1) Dynamic Application Security Testing (DAST)
DAST is also referred to as black-box testing which is the analysis of an application in use. Unlike SAST which emphasizes code and actual source code changes, DAST focuses on testing operating systems through various attacks such as SQL injection, and cross-site scripting as well as checking general information security. In terms of security vulnerabilities, it is quite good. In certain security measures, security and vulnerability are shrouded with uncertainties. It gives a more precise evaluation.
2) Static Application Security Testing (SAST)
One major benefit of SAST is that it helps developers catch and fix vulnerabilities early, saving time and money down the line. However, it doesn’t identify issues that occur during runtime, so it's often used alongside other testing methods.
3) Penetration Testing
Penetration testing, also known as ethical hacking, simulates real-world attacks on an application to find and exploit vulnerabilities. Unlike automated tools, this testing requires skilled testers who can think like attackers and spot weaknesses that might go unnoticed by other methods.
Penetration tests can be done from different angles:
Black box: No prior knowledge of the app.
White-box: Full knowledge of the app.
Gray-box: Some knowledge of the app.
The goal is to uncover vulnerabilities that could lead to unauthorized access or data breaches. This testing is usually done at the end of the development cycle, just before the app is launched.
4) Security Code Review
A security code review is the process of manually examining an app's source code to find security vulnerabilities. While automated tools can catch common issues, a manual review can identify more complex problems that need human insight. Security to safeguard users' data should be involved in the whole mobile application lifecycle.
See Also- Mobile App Testing: Benefits, Tools, and Best Practices
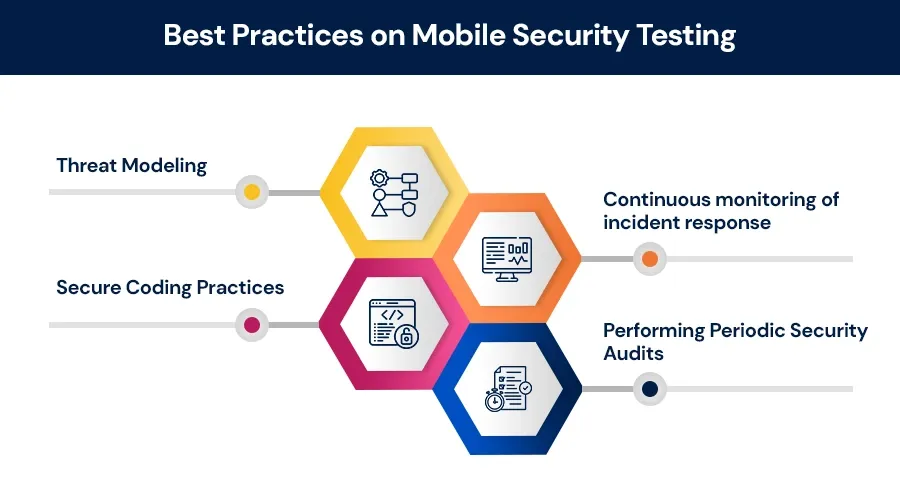
Best Practices for Mobile Security Testing
Security issues need to be caught in the design and coding phase itself to minimize the risk of defects in the final product help. Below are some best practices concerning security testing.
1. Threat Modeling
Threat modeling is effective at trying to identify and mitigate security threats early in the development cycle before they have a chance of getting dangerous. Design the application architecture by identifying potential attack vectors, such as insecure APIs or inefficient authentication mechanisms. Controlling these risks is by security. This should be an ever-evolving process for changing applications and emerging threats.
2. Secure Coding Practices
Following safe coding practices reduces the number of vulnerabilities in your application code. Developers should use standard approaches and guidelines, such as the OWASP Mobile Security Project, when writing secure and clean code to prevent injection. It remains in a static state when transmitted.
Here are some important practices to follow for secure coding:
1. Input Validation:
Always validate and sanitize user inputs to prevent injection attacks.
2. Authentication and Authorization:
Use strong authentication methods and ensure users have the right access levels for the app's features.
3. Encryption:
Protect sensitive data by using encryption, both when it's being transmitted and when it's stored.
4. Error Handling:
Implement proper error handling to keep attackers from gaining insights into the app's internal workings.
3. Performing Periodic Security Audits
Security Audit: This entails a critical look at the security features of an application to find the weak points, with a view to their compliance with mobile app security standards. Regular security audits by independent security experts will provide unbiased insight into application security.
Burnout: Results analysis shall be used to prioritize improving security and addressing the issues identified. Continuous monitoring of incident response.
4. Continuous Monitoring of Incident Response
Security in no way stops at the moment of an application going into production. There should be continuous monitoring to ensure the detection of security incidents and thus responding quickly. The developers should therefore make use of monitoring tools that can notice with ease unusual activity such as unauthorized access or data deletion.
The plan should explain the roles to be played in case of a breach, such as notifying the affected users, mitigating the breach, and conducting some sort of post-incident investigation to prevent any future occurrences. While security testing plays a significant role in securing user data, it also has challenges of its own.
Here are some of the common problems faced in mobile security testing:
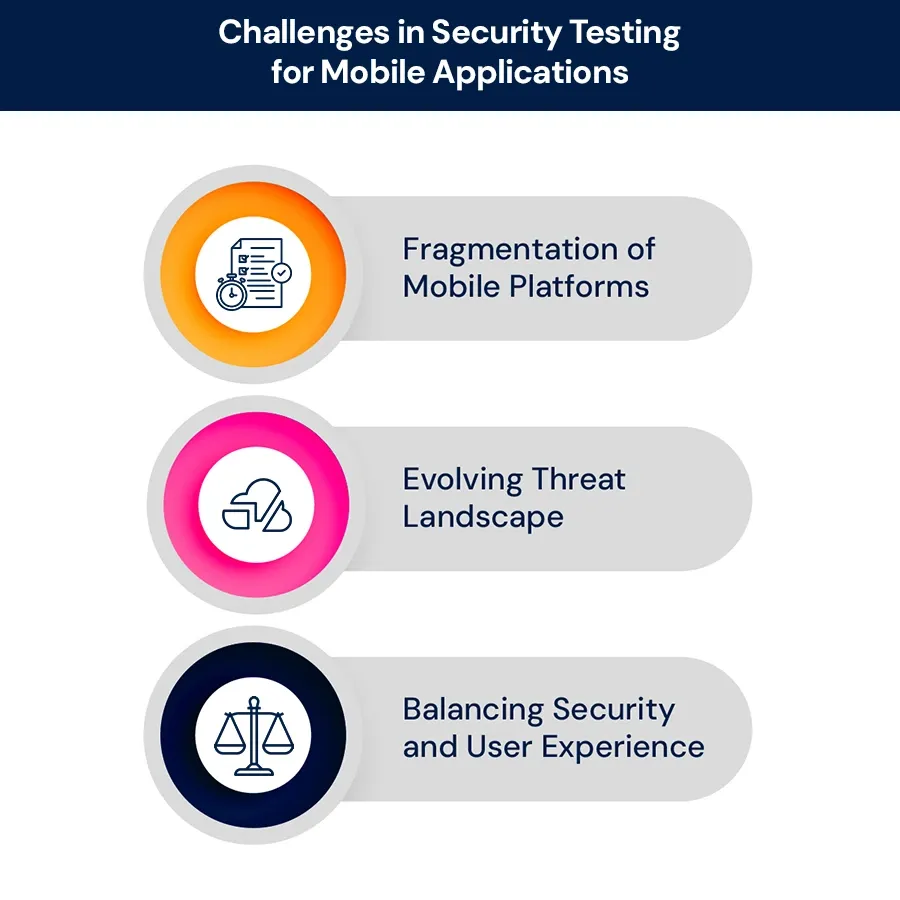
Challenges in Security Testing for Mobile Applications
While mobile app security testing is crucial for protecting user data, it comes with its challenges. Here are some of the key issues faced when testing the security of mobile apps:
1. Fragmentation of Mobile Platforms
The mobile ecosystem is very fragmented, running on multiple operating systems, including Android and iOS, each available in many different product models. All the different platforms have their own security features and vulnerabilities, making testing of the security on each device and testing on the platform cumbersome. This will also help in improving the mobile security testing process by emulation of different tools with automated testing tools.
2. Evolving Threat Landscape
The mobile application threat landscape is constantly updated with new vulnerabilities and changes in attack strategies. This requires continuous learning and adaptation. On the tool side, mobile security testing tools will need periodic updating to keep pace with the changing landscape of new vulnerabilities.
3. Balancing Security and User Experience
Sometimes, security measures can make using an app frustrating, which may lead users to avoid it.
To find the right balance between security and user experience, developers should focus on user-friendly design and conduct usability tests to pinpoint any issues. Security features should be implemented in a way that feels seamless and unobtrusive, while still offering strong protection.
See Also: Understanding AI Security
Conclusion:
Protecting user data is important, particularly for mobile applications. Mobile Application Testing Services help identify and fix security flaws early in development. By testing for issues including insecure storage of data, inadequate encryption, and poor user authentication; by knowing about them, developers can avoid security threats. These services ensure your app meets industry standards and keeps user data safe, building trust and improving security.
With data breaches becoming more common, it's essential to follow best practices in app security testing. This includes checking API testing security, for vulnerabilities like SQL injection and cross-site scripting (XSS), and ensuring data encryption. Tools like OWASP ZAP and Burp Suite help developers spot weaknesses and improve app security.
Mobile application pen-testing (penetration testing) simulates real-world attacks to find any security gaps. Regular security testing of mobile apps ensures that apps meet mobile security standards, protecting both user data and the app’s reputation.
As mobile technology evolves, security threats change too. Ongoing mobile security testing and updating security testing tools are key to keeping apps safe. Investing in security not only prevents breaches but also builds trust with users, ensuring long-term success.
Ensure Your App’s Security Now Our Experts